In the 21st Century, people have become more and more connected with technology, entangling their lives in the physical world with their digital ones. Being able to protect yourself physically has always been important, and in this day and age, being able to protect yourself online is critical.
As a kid with an interest in technology and Cybersecurity, I have talked to many people about their digital security practices. To be honest, some of what I have seen horrifies me, and don’t even get me started on the nightmare scenario – a simple password, lacking length and randomization, being reused on virtually every account the person owns, including sensitive accounts, such as online banking and brokerage accounts. If your Gmail password is “Gmail[birth year]!” and your Netflix password is “[city of birth][year of birth]!” this article is for you.
A strong password is the crux of your digital identity. Most account takeovers don’t even happen via phishing, they happen through the use of stolen or leaked credentials. For example, let’s take a look at this “hypothetical” scenario. At some point before April, 2019, you sign up for a Lumin PDF account using your school email, cplager25@dths.org. In September of 2019, Lumin PDF reveals that they had been breached back in April, but only after the sale of their internal database containing 15.5 million records of user data appeared for sale on a popular hacking forum. This breach, they report, contains Authorization tokens, Email addresses, Genders, Names, Passwords, Spoken languages, and Usernames. Unfortunately, your Lumin PDF and Google password were the same, and now hackers have breached your Google Docs account and stolen your secret diary.
This is very upsetting and tragic, but obviously a hypothetical scenario. Password breaches are scary, especially because it is something out of your control, but by following the tips in this article, you will be able to feel more confident and secure knowing you have lessened the degree to which leaked credentials will affect your digital life as a whole.
Tip #1: Check for Breached Passwords
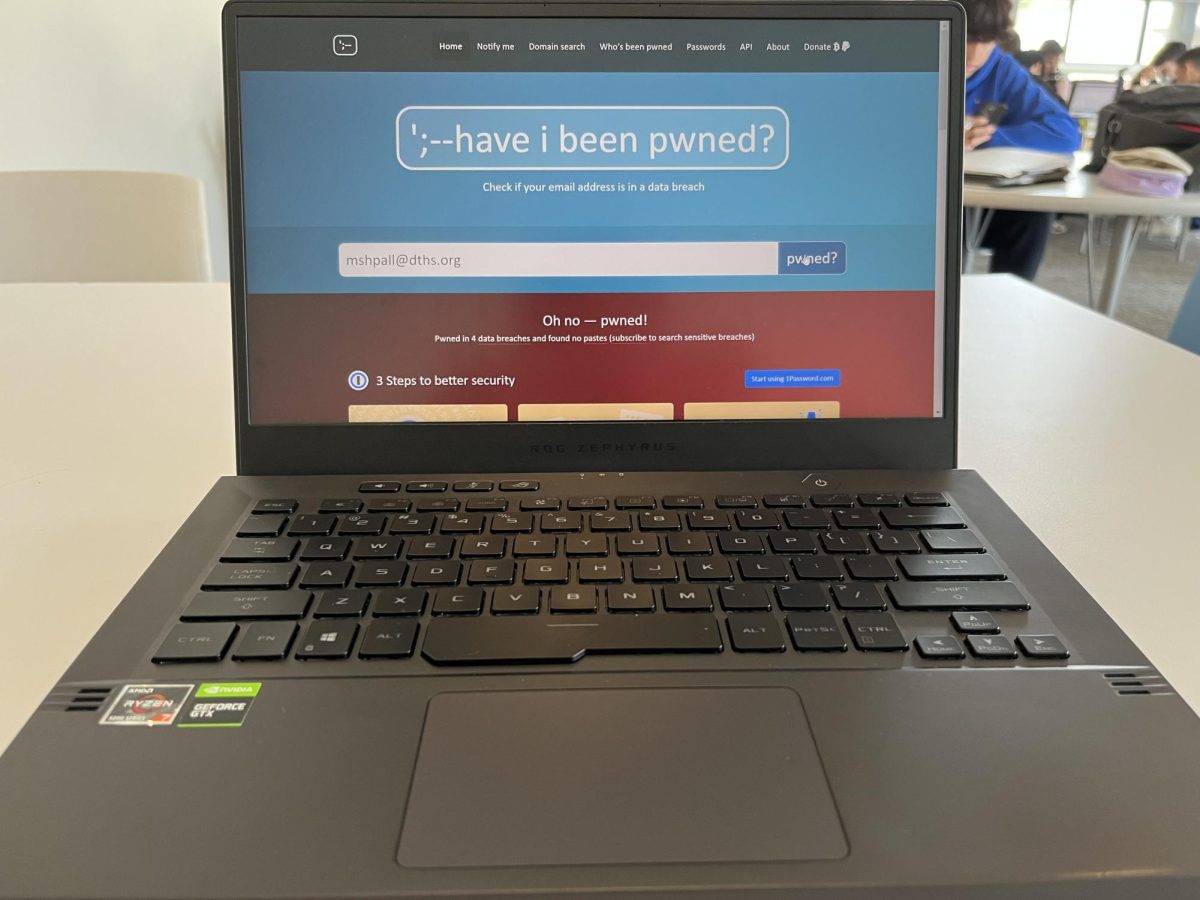
You can check if your email has been involved in a data breach by going to haveibeenpwned. This website will show the data breaches your email has been involved in, allowing you to recognize the breached password and take action if you have reused the same email:password combination on other websites.
Tip #2: Learn to Create Strong Passwords
You can check the strength of your current passwords using security.org’s free online tool, found here.
Security.org also includes a list of password best practices, which are:
- A password should be 16 characters or more; our password-related research has found that 45 percent of Americans use passwords of eight characters or less, which are not as secure as longer passwords.
- A password should include a combination of letters, numbers, and characters.
- A password shouldn’t be shared with any other account.
- A password shouldn’t include any of the user’s personal information like their address or phone number. It’s also best not to include any information that can be accessed on social media like kids’ or pets’ names.
- A password shouldn’t contain any consecutive letters or numbers.
- A password shouldn’t be the word “password” or the same letter or number repeated.
Tip #3: Use a Password Manager
Using a password manager such as 1password can keep you safe online by helping you generate complex, unique passwords for each of your online accounts. This method provides you with the convenience of only remembering one password (the master password to unlock your password manager), while providing the security of having multiple, random passwords which would be extremely difficult for the average person to memorize.
Tip #4: Use an Authenticator App
Most websites allow you to add an Authenticator App such as Microsoft or Google Authenticator. This provides you with a randomly generated code every 30 seconds, and the code never leaves your device. Even if the hacker does have your valid email:password combination, they will not be able to log in to your account without your device. Instructions on how to set up an authenticator app can be found online.
By following these tips, you can ensure peace of mind when navigating the complex world of digital security.